NSX
VMware NSX Network
Virtualisation and Security Platform
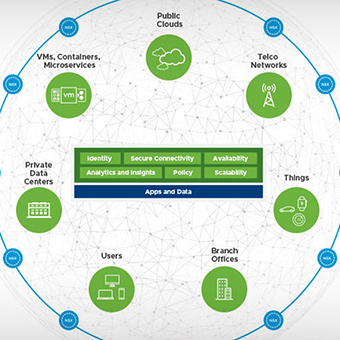
NSX enables the creation of entire networks in software and embeds them in the hypervisor layer, abstracted from the underlying physical hardware. All network components can be provisioned in minutes, without the need to modify the application.
NSX is now also availble as a service: VMware NSX Cloud delivers consistent networking and security for cloud-native applications. The service improves operational scalability, control, and visibility – with lower OpEx – across native public clouds such as AWS. Visit the new NSX Cloud page for more information.
What's New:
NSX SD-WAN Leads the Industry »VMware is named a Leader in the 2018 Gartner Magic Quadrant on WAN Edge Infrastructure.
Announcing NSX-T Data Centre 2.3 »Learn what NSX-T delivers for applications and data across any environment.
Adaptive Micro-Segmentation »Take application security beyond micro-segmentation.
NSX Mindset »See how network professionals have transformed their career trajectory with VMware NSX.
Security
NSX embeds security functions right into the hypervisor. It delivers micro-segmentation and granular security to the individual workload, enabling a fundamentally more secure data center. Security policies travel with the workloads, independent of where workloads are in the network topology.
Application Continuity
NSX abstracts networking from the underlying hardware and attaches networking and security policies to their associated workloads. Applications and data can reside and be accessible anywhere. Move workloads from one data center to another, or deploy them into a hybrid cloud environment.
Automation
NSX lets you treat your physical network as a pool of transport capacity, with network and security services attached to workloads using a policy-driven approach. This automates networking operations and eliminates bottlenecks associated with hardware-based networks.
Compliance
NSX enables micro-segmentation and granular security of workloads in virtualised networks, isolating sensitive systems and reducing both risk and scope of compliance. Use NSX to help ensure and demonstrate compliant operations with many regulations such as PCI DSS, HIPAA, FedRAMP, SOC, CJIS, DISA STIG and more.
Getting Started
RESOURCES
Learn and Evaluate
- NSX Data Center Product Datasheet
- NSX Data Center Solution Overview: Accelerating the Business
- Operationalizing VMware NSX Guide
- Building VMware NSX Powered Clouds and Data Centers for Small and Medium Businesses Guide
- Blog: The Virtual Cloud Network Demystified
- Network Virtualization Fundamentals Guide
Plan and Design
- NSX Data Center Quick Start Guide
- VMware NSX-T Reference Design
- VMware NSX for vSphere Network Virtualization Design Guide
- Multi-site Options and Cross-VC NSX Design Guide
- Security for Hyper-Converged Solutions
- NSX Small Data Center Design Guide
- Deploying NSX with Cisco UCS and Nexus 9000 Infrastructure Design Guide
- VMware NSX running on a Cisco ACI Underlay Fabric Design Guide